Keestash integrates LDAP authentication into it’s eco-system, enabling the integration of LDAP based login.
As an enterprise ready using industrial standards, Keestash is aware of the strategic importance of integrating legacy systems and proven and established systems.
Install LDAP app
The LDAP app is for enterprise subscriptions only. To enable the LDAP app, the delivered app folder must be placed under <documentRoot>/apps. Keestash recognizes the app automatically.
apps folder, Keestash needs to run migrations in order to create the necessary database tables. Find more about database migrations here.Check LDAP app installation
There are multiple ways to check whether the LDAP app is installed. The easiest way is to use the Keestash CLI tool (more about Keestash CLI here). The following command lists all installed apps, where the LDAP app has to be part of:
sudo -u www-data php bin/console.php apps:list
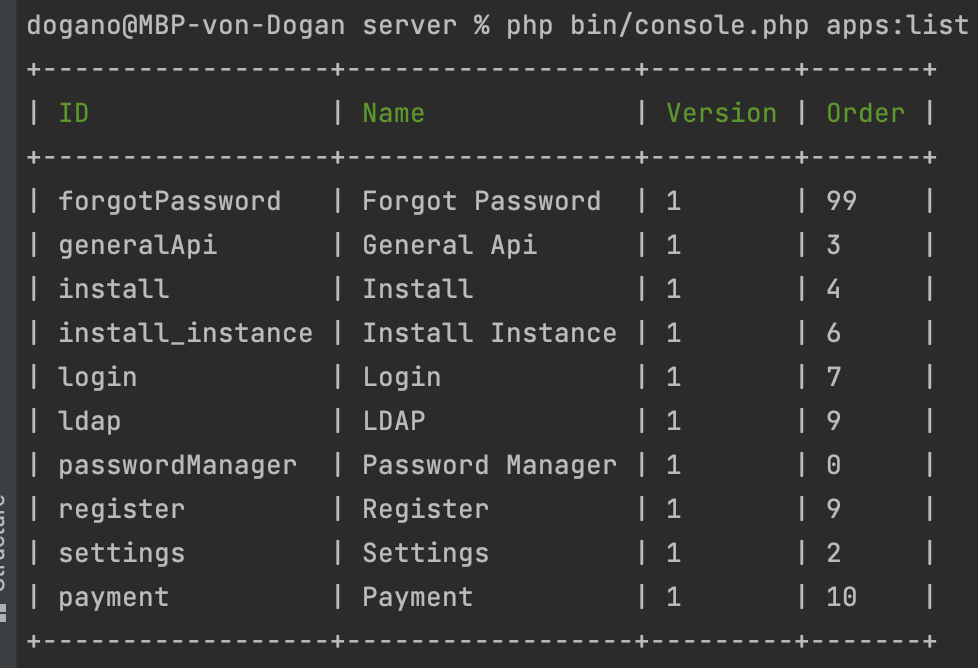
If ldap is listed in the result, the LDAP app is installed.
Configure LDAP
There are three main CLI commands to configure LDAP, one for connecting, one for disconnecting Keestash to an existing LDAP server and the last one to configure LDAP options:
sudo -u www-data php bin/console.php ldap:server:create
The create command asks for several details:
| Host | The host name or IP address of the LDAP server. |
| Port | The port on which to connect to the LDAP server. |
| DN | The name as DN of a user who has permissions to do searches in the LDAP directory. |
| Directory Base DN | The base DN of LDAP, from where all users and groups can be reached. |
| Password | The users password |
After submitting the information, Keestash first checks whether an existing Keestash configuration exists. If this is the case, it is not possible to connect to a second LDAP server. If you want to connect Keestash to another LDAP server, you need to remove the existing one first.
The LDAP configuration is configured and Keestash triggers the sync process to import user (technically: an event is triggered that – among others – has an sync users listener).
The sync users process connects against the LDAP server and lists all users. The user has to have at least the following attributes:
| uid | an unique identifier, used for the username |
| the user’s email address, used for the email address | |
| telephoneNumber | the user’s phone number, used for the phone number |
If the attributes above does not exist, Keestash assumes that the user is not valid and simply skips.
The next step is check the attributes mentioned above. While LDAP provides multiple values per attribute, we simply take the first one.
If the uid and email address already exists, Keestash does not create these users. Instead, the users are written into a temporary table to get handled manually by the administrator.
Since a LDAP server provides less information, Keestash decided to make some default vaules. While this seems to be unusual, they are technically just needed to create the user.
Show LDAP Configuration
Sometimes, admins need to show the current LDAP configuration. By using the command below, the LDAP host can be shown in order to get to know whether a LDAP backend is connected or not:
sudo -u www-data php bin/console.php ldap:server:show
The command shows an error if the instance is not installed at all or there is no LDAP configured. If LDAP is configured, the command displays the LDAP host.
Remove LDAP connection
sudo -u www-data php bin/console.php ldap:server:remove
The remove command needs the hostname as an argument. Keestash deletes the LDAP connection and their respective users if the a configuration for the host is found. Otherwise the command throws an error.
Configure LDAP options
sudo -u www-data php bin/console.php ldap:option
The following options are available:
| restrict-local-accounts | Boolean | true/false |
Final Notes
For security reasons, Keestash does not allow anonymous logins.